Key Takeaways
- Cybersecurity is critical in safeguarding digital systems, data, and networks from a wide range of threats like malware, phishing, and DDoS attacks.
- The field includes various specialized areas such as network security, cloud security, and endpoint protection, each with unique strategies and tools.
- Strong cybersecurity practices—like using strong passwords, enabling multi-factor authentication, and regularly updating systems—are essential for defense.
In an era where everything from banking to binge-watching relies on digital networks, cybersecurity has become more than a buzzword—it’s a necessity. But what is cybersecurity?
Cybersecurity is fundamentally about safeguarding systems, networks, and data against digital threats and attacks. As our reliance on technology grows, so do the risks of breaches, identity theft, and cyberattacks.
Now more than ever, understanding cybersecurity is essential. So, let’s break down what cybersecurity involves and explain why it matters more than ever.
What Is Cybersecurity?
Cybersecurity is the practice of defending computers, servers, networks, and data from unauthorized access or attacks. It’s all about keeping digital information safe and making sure systems work the way they’re supposed to. As more of our lives move online, the need to protect this digital space becomes increasingly important—for individuals, businesses, and even governments.
At a high level, cybersecurity works by combining technology, processes, and people. Tools like firewalls, encryption, and antivirus software help block threats; policies and best practices guide how organizations and users handle data responsibly; and cybersecurity professionals—many trained in programs like those at Syracuse University’s School of Information Studies—design systems and strategies that stay one step ahead of attackers.
Why Is Cybersecurity Important?
Cybersecurity matters because nearly every part of modern life depends on digital systems. From online banking and social media to hospital records and national defense, data is constantly being stored, shared, and targeted. Without strong protection, these systems are vulnerable to cyberattacks that can result in data breaches, financial loss, identity theft, and even damage to an organization’s reputation.
For businesses, a single breach can cost millions and destroy customer trust. For governments, it can threaten national security, and for individuals, something as simple as a stolen password can disrupt your life in seconds. With the rise of remote work, cloud computing, and AI, cybercrime is growing at an alarming rate—making cybersecurity more urgent than ever.
Types of Cybersecurity
Cybersecurity isn’t a one-size-fits-all solution. It includes several specialized areas, each focused on protecting a specific part of our digital world—from networks and applications to cloud systems and mobile devices.
Network security
Network security is the practice of protecting the usability, reliability, and integrity of a network and its data. It involves both hardware and software technologies that block unauthorized access and detect potential threats.
Common tools include firewalls, which act as barriers between trusted and untrusted networks, and intrusion detection/prevention systems (IDS/IPS), which monitor traffic for malicious activity.
Effective network security ensures that data flows safely and that organizations can maintain continuous, secure communication across their digital environments.
Information security
Information security focuses on protecting data from unauthorized access, modification, or destruction, whether it’s stored digitally or physically. Core practices include data encryption, access controls, and clear data classification to determine levels of protection based on sensitivity.
Crucial across every industry, this form of cybersecurity helps prevent data breaches and maintain trust in the systems that store and handle valuable information. At its foundation is the CIA triad: confidentiality (keeping information private), integrity (ensuring data is accurate and unaltered), and availability (making sure data is accessible to authorized users).
Cloud security
Cloud security refers to the technologies and practices used to protect data, applications, and services hosted in cloud environments. As businesses increasingly rely on cloud providers, the shared responsibility model becomes key—cloud vendors secure the infrastructure while customers secure their data and configurations.
Best practices include setting up secure cloud configurations, monitoring for unusual activity, and using provider-specific tools like AWS Shield or Azure Defender. Ultimately, cloud security ensures that as organizations scale and adopt flexible, remote-friendly systems, their critical assets remain protected from cyber threats and accidental exposure.
Endpoint security
Endpoint security protects user devices such as laptops, smartphones, and desktop computers—essentially the front lines of cybersecurity. Each device represents a potential entry point for attackers, so tools like antivirus software, mobile device management (MDM), and endpoint detection and response (EDR) are used to monitor and secure them.
As remote work becomes more common, securing endpoints is more important than ever. Employees often access sensitive systems from outside secure networks, increasing risk. Strong endpoint security helps prevent data breaches, malware infections, and unauthorized access, keeping systems and users safe regardless of location.
Application security
Application security involves building and maintaining software that can resist threats. This includes implementing secure coding practices during development, regularly scanning for vulnerabilities, and applying patches to fix security flaws. Strong application security ensures that both internal tools and customer-facing apps function safely and without exposing sensitive information.
Tools such as web application firewalls (WAFs) help defend against attacks like SQL injection or cross-site scripting. Developers play a vital role, especially in DevSecOps environments, where security is integrated into every stage of the software development lifecycle.
Zero trust security
Zero trust security is based on the “never trust, always verify” principle. Instead of assuming users or devices inside a network are safe, zero trust requires continuous authentication and strict access controls. Every user, device, or system must prove that it is trustworthy before gaining access to resources.
Techniques like microsegmentation, identity verification, and least-privilege access are employed to limit the impact of a breach. Unlike traditional perimeter-based models, zero trust treats every access request as a potential threat. This modern approach enhances security across distributed systems, especially in environments with remote work, cloud platforms, and mobile access.
Operational technology (OT) security
OT security focuses on protecting the hardware and software used to control physical processes in sectors like manufacturing, utilities, and transportation. These environments often use SCADA (supervisory control and data acquisition) systems and IoT or industrial IoT (IIoT) devices to monitor and manage machinery in real time.
Cyberattacks on OT environments—such as factories, utilities, or transport systems—can halt production, damage machinery, or even pose risks to human safety. That’s why strong OT security is essential: it protects critical infrastructure from digital threats and ensures that real-world operations remain stable, secure, and uninterrupted.
Common Cybersecurity Threats
Cyber threats come in many forms, constantly evolving to exploit weaknesses in systems, people, and technologies. These threats target everything from cloud environments and personal devices to entire networks. Below, we explore some of the most pressing cybersecurity threats organizations face today.
Vulnerabilities in cloud security
Cloud environments face unique risks due to their scale and accessibility. One common issue is misconfigured cloud settings, which can leave sensitive data publicly exposed. Insecure application programming interfaces (APIs) also pose threats by offering attackers a potential way in.
Then, there is data loss, which can occur from accidental deletion, poor backup practices, or unauthorized access. Securing these environments requires constant monitoring and strict access controls to avoid exploitation.
Insider threats
Insider threats arise when people within an organization—such as employees, contractors, or partners—intentionally or unintentionally compromise security. Malicious insiders might steal sensitive data or sabotage systems for personal gain or revenge. Such threats are becoming more common, as 85% of organizations have experienced insider threats at least once.

Unlike external threats, insider attacks exploit trust, making them particularly dangerous and difficult to anticipate. But even well-meaning staff can pose risks by falling for phishing emails, misplacing devices, or mishandling information.
That is why monitoring behavior, limiting privileges, and promoting security awareness are key strategies for minimizing insider-related incidents.
Malware
Malware refers to harmful software created to interfere with, damage, or illegally access computer systems. Common types include viruses, worms, and Trojans, each spreading and operating differently. Recent statistics demonstrate a staggering 6.06 million malware attacks detected worldwide.
Malware is often delivered through email attachments, infected websites, or USB drives. Once inside, it can steal data, spy on users, or even destroy files. Polymorphic malware, which changes its code to evade detection, is especially a well-known concern.
Attackers frequently use malware to infiltrate organizations, exfiltrate data, or demand ransom. Effective defenses include updated antivirus tools, strong user training, and regular system monitoring.
Phishing
Phishing attacks use deceptive messages—often emails or texts—to trick users into revealing sensitive information like passwords, credit card numbers, or login credentials. These messages may appear to come from trusted sources, creating a false sense of urgency or legitimacy. Approximately 3.4 billion spam emails get sent every day, making phishing a valid concern for businesses.
Spear phishing targets specific individuals with personalized messages, while business email compromise (BEC) involves attackers posing as executives to manipulate employees. As phishing remains one of the most successful attack methods due to its simplicity and reliance on human error, educating users and implementing email filters can significantly reduce risk.
Ransomware
Ransomware is a type of malware that locks or encrypts a victim’s data and demands payment—often in cryptocurrency—for its release. Attackers typically gain access through phishing emails, unpatched vulnerabilities, or compromised remote desktop services. Regular backups, patch management, and incident response plans are crucial defenses.
The effects of ransomware can be devastating: organizations may lose access to vital systems, suffer major financial losses, and face public scrutiny. In some cases, paying the ransom doesn’t guarantee data recovery. Well-known cases like WannaCry and REvil have shown just how disruptive ransomware can be.
Social engineering attacks
Social engineering attacks exploit human psychology rather than technical vulnerabilities. Attackers manipulate people into sharing confidential information or granting access. Tactics include pretexting (creating a fabricated scenario), baiting (offering something tempting), tailgating (following someone into a secure area), and impersonation (posing as a trusted figure).
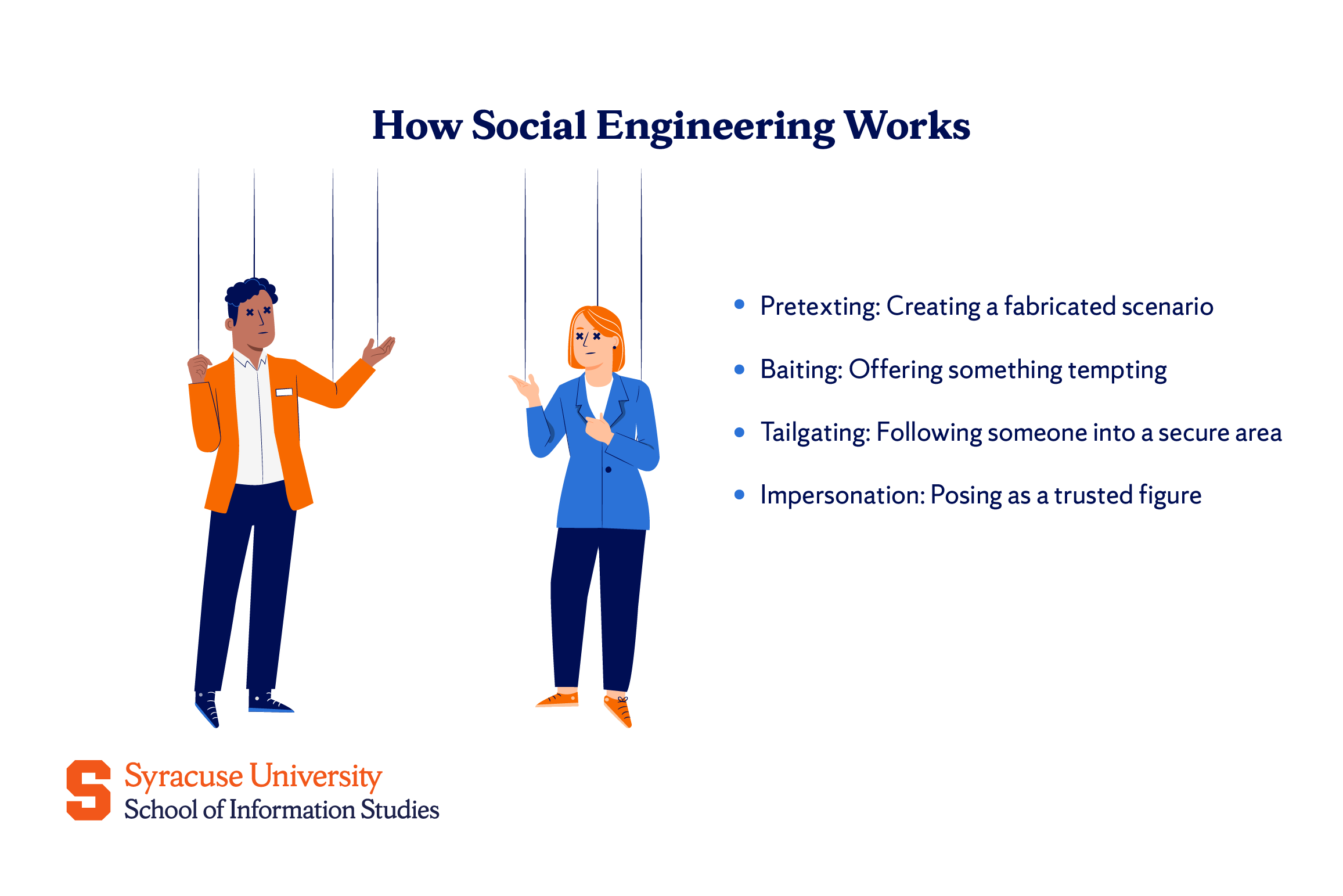
Social engineering is often the first step in more complex breaches. These attacks work because they target emotions like fear, trust, or curiosity. Training employees to recognize suspicious behavior and verify identities is essential to prevent these low-tech but highly effective threats.
Distributed denial of service (DDoS)
DDoS attacks are designed to take down websites or online services by flooding them with too much traffic at once. This traffic usually comes from many infected devices (called a botnet), all sending fake requests to overwhelm the system.
Some attacks use amplification, where attackers trick other servers into sending even more traffic, while others target specific parts of a website to slow it down. These attacks can crash websites, cause financial loss, and hurt a company’s reputation. To defend against them, organizations use tools like rate limiting, load balancing, and content delivery networks (CDNs).
Detecting and Responding to Cyber Threats
Spotting threats early is essential for stopping attacks before they do serious harm. Threat detection works by constantly monitoring systems for unusual activity, unauthorized access, or known signs of attack. Tools such as Security Information and Event Management (SIEM) systems gather and analyze data across an organization to uncover potential risks.
Threat intelligence—insights into new threats and hacker methods—is also applied to keep security teams one step ahead. Anomaly detection, on the other hand, adds another layer by flagging unusual behavior that might otherwise go unnoticed. The faster threats are found, the quicker teams can respond and reduce the damage caused by cyber incidents.
Best Practices for Cybersecurity
Improving your cybersecurity doesn’t have to be complicated. Here’s a practical checklist to help strengthen it:
- Use strong, unique passwords for every account, and store them in a password manager.
- Enable multi-factor authentication (MFA) to add an extra layer of protection beyond passwords.
- Keep software and devices updated to fix security vulnerabilities as soon as patches are released.
- Train users regularly to spot phishing emails, suspicious links, and social engineering attempts.
- Create and test an incident response plan, so everyone knows how to react during a cyberattack.
- Back up important data often and store backups in a secure, separate location.
- Limit access to sensitive information using role-based permissions—only give users what they need.
The Essential Takeaways on Cybersecurity
Cybersecurity is essential in today’s connected world, where digital threats are constantly evolving. From malware to insider attacks, risks come in many forms, but strong defenses can help protect systems and data. Staying secure requires ongoing awareness, smart tools, and continuous learning.
As threats become more sophisticated, so must our strategies. The Bachelor’s Degree in Information Management and Technology at Syracuse University, as well as the Certificate of Advanced Study (C.A.S.) in Information Security Management, prepare students to meet these challenges head-on, providing the knowledge and skills needed to lead in cybersecurity and create safer, more resilient digital environments.
Frequently Asked Questions (FAQs)
Do I need a degree to work in cybersecurity?
You don’t strictly need a degree to work in cybersecurity, but having one gives you a strong advantage. It opens more career opportunities, helps you advance faster, and gives you a deeper understanding of both the technical and strategic sides of cybersecurity.
What skills are required for cybersecurity?
Cybersecurity requires strong problem-solving and critical thinking skills, a solid understanding of networks and systems, and hands-on experience with tools like firewalls, intrusion detection systems, and antivirus software.
How much do cybersecurity professionals earn?
Salaries vary, but many roles offer $111,000 to $150,000 annually, depending on experience and specialization.
Is cybersecurity a good career choice?
Yes—it offers strong job prospects, competitive salaries, and the chance to make a meaningful impact by protecting the digital world.
