Key Takeaways
- The average downtime after a ransomware attack is 24 days.
- 74% of breaches involve human error, privilege misuse, or stolen credentials; all issues that can be avoided with proper security practices.
- The CIA triad (confidentiality, integrity, and availability) forms the foundation of effective data security strategies.
- Organizations must implement frameworks like ISO/IEC 27001 and NIST, combined with practical tools like IAM, DLP, and SIEM systems, to safeguard data.
In 2025, the average cost of a data breach reached $4.4 million, according to IBM’s Cost of a Data Breach Report. Beyond financial losses, breaches undermine customer confidence and can lead to severe regulatory penalties that disrupt business operations overnight. As organizations handle increasing volumes of sensitive information, data security management has become a business-critical priority.
Data security management isn’t just about installing antivirus software or setting passwords. It’s a complete approach including strategic planning, policy creation, and technology deployment to protect data. Whether you’re a small business owner or an IT professional at an enterprise, understanding how to secure your data means protecting your operations, reputation, and bottom line.
What Is Data Security Management?
Data security management is the practice of protecting digital information from unauthorized access, corruption, theft, and loss throughout its entire lifecycle. It combines policies, procedures, and technologies to ensure that sensitive data remains secure whether it’s stored on-premises, in the cloud, or transmitted across networks.
While cybersecurity focuses broadly on protecting systems and networks, data security management specifically targets the information itself, ensuring that only authorized users can access it, that it remains accurate and unaltered, and that it’s available when needed.
At its core, data security management serves as the foundation for regulatory compliance, business continuity, and customer trust. Organizations that implement strong data security practices can prevent costly breaches, meet legal requirements like GDPR or HIPAA, and maintain the confidence of customers and partners who entrust them with sensitive information.
Why Data Security Management Matters
The risks of weak data security are greater than ever. According to Verizon’s Data Breach Investigations Report, 74% of breaches involve human error, privilege misuse, or stolen credentials; all issues that can be avoided with proper security practices.
When organizations fail to protect data, the effects spread across many areas:
Financial impact: Beyond the immediate costs of breach response and recovery, organizations face regulatory fines that can reach millions. Under GDPR, companies can be fined up to 4% of annual global revenue or €20 million, whichever is higher. Healthcare organizations violating HIPAA face penalties up to $1.5 million per violation.
Trust and reputation: Customer trust that takes years to earn can disappear after one breach. A 2024 survey by PwC found that 87% of consumers would take their business elsewhere after a data breach. The reputational damage often exceeds direct financial losses, affecting stock prices and market position.
Operational continuity: Ransomware attacks can shut down operations for days or weeks. The average downtime after a ransomware attack is 24 days. For businesses dependent on real-time operations, this disruption can be catastrophic.
Effective data security management transforms these risks into competitive advantages. Organizations with strong security practices can prove compliance and lower insurance costs.
Key Objectives: The CIA Triad
Data security management rests on three fundamental objectives known as the CIA triad: confidentiality, integrity, and availability. These principles guide every security decision and technology choice.
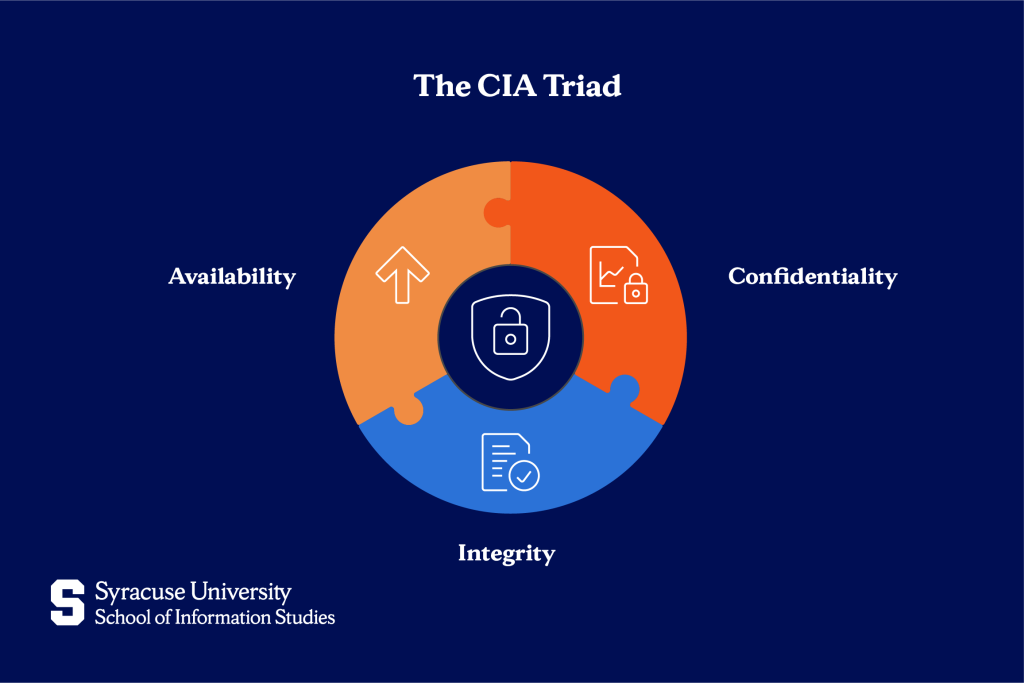
Confidentiality ensures that sensitive information remains accessible only to authorized individuals. Organizations achieve this through encryption, access controls, and authentication systems. For example, healthcare providers use role-based access control (RBAC) to ensure that nurses can view patient records relevant to their assigned patients, but not unrelated files.
Integrity ensures data stays accurate and unchanged unless approved. Hash functions and digital signatures help confirm files haven’t been altered while stored or sent. Banks use these controls to make sure transaction records can’t be changed later.
Availability means that authorized users can access data and systems when they need them. This includes protection against service disruptions, like hardware failures, cyberattacks, or natural disasters. Cloud providers keep services running through backup systems, automatic data copies, and recovery plans that can restore access within minutes.
Balancing these three goals takes careful planning. Too much focus on confidentiality can compromise availability, while prioritizing availability without access controls can weaken confidentiality. Effective data security management finds a middle ground that fits the organization’s needs and risk tolerance.
Key Components, Frameworks, and Tools
Data security management operates through several interconnected components that work together to protect information.
Core components:
- Governance and policy set clear rules for how data is handled, who can access it, and how to respond to breaches. Data classification policies designate sensitivity levels and specify required protections.
- Access control implements least privilege principles, giving users only the permissions they need. Multi-factor authentication and zero-trust models confirm every access request, no matter where it comes from.
- Encryption protects data both when stored and when sent. AES-256 keeps stored data safe, while TLS 1.3 secures information as it moves across networks.
- Monitoring and response identify suspicious activities through continuous surveillance. Security Information and Event Management (SIEM) systems collect logs, link related events, and alert teams about possible threats.
Frameworks:
- ISO/IEC 27001 provides a complete framework for establishing and maintaining an Information Security Management System (ISMS). The standard covers 14 control domains and requires regular audits.
- The NIST cybersecurity framework organizes security activities into five functions: identify, protect, detect, respond, and recover. Many U.S. federal agencies use NIST as their primary security guide.
Tools and technologies:
- Identity and Access Management (IAM) systems control resource access through single sign-on, automated provisioning, and adaptive authentication that adjusts based on context.
- Data Loss Prevention (DLP) tools monitor data movement to prevent unauthorized sharing, blocking activities like emailing confidential documents to personal accounts.
- SIEM systems aggregate log data from across the IT environment, using machine learning to establish baselines and flag anomalies that might signal attacks.
Implementing Data Security Management
Moving from theory to practice requires a systematic approach. Organizations that follow these steps can build security programs that grow with their needs.
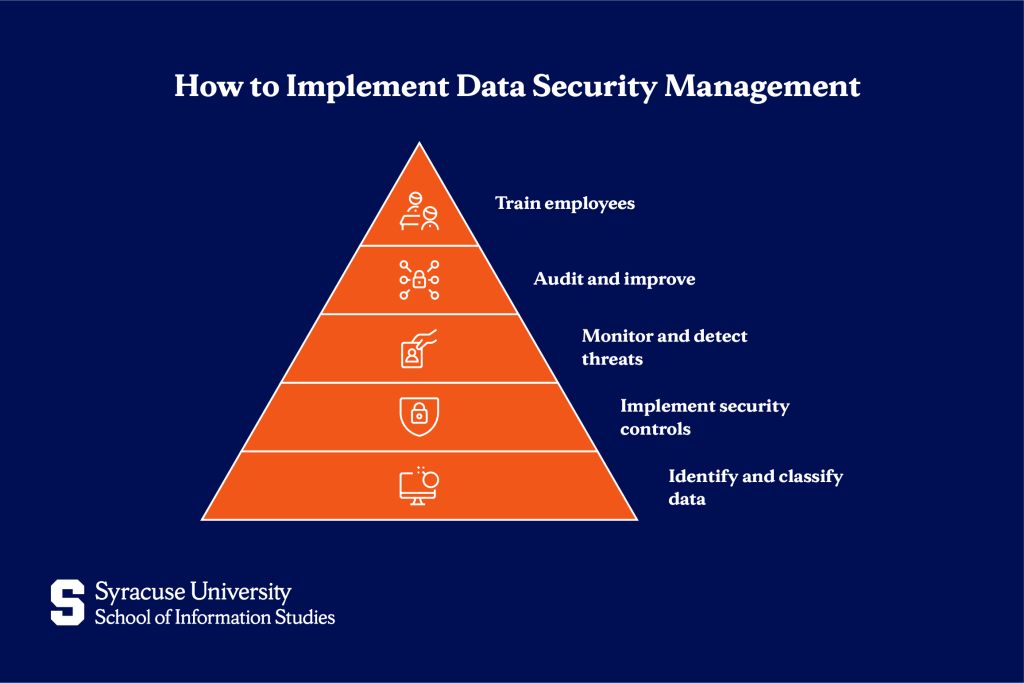
1. Identify and classify data
Conduct a complete inventory of your data assets. Map where sensitive information lives (in databases, file shares, email systems, and cloud applications). Classify data based on sensitivity: public, internal, confidential, and highly confidential. This classification guides every security decision.
2. Implement security controls
Based on data classification, apply appropriate protective measures. Encrypt highly confidential data, restrict access using role-based permissions, and deploy multi-factor authentication. Configure firewalls and endpoint protection on all devices that touch sensitive data.
3. Monitor and detect threats
Deploy monitoring tools across your environment and configure alerts for suspicious patterns. Watch for failed login attempts, unusual data transfers, and access from unexpected locations. Create an incident response plan before you need it, defining roles and containment steps.
4. Audit and improve
Schedule regular security audits and third-party assessments. Test controls through vulnerability scans and penetration tests. Review access permissions quarterly to remove unnecessary privileges. Track metrics like time to detect threats and percentage of systems encrypted.
5. Train employees
Implement security awareness training covering password management, phishing identification, and data handling procedures. Test training through simulated phishing campaigns. Create a security-conscious culture where employees report suspicious activities without fear.
Common Challenges in Data Security Management
Even well-intentioned security programs face obstacles that can undermine effectiveness.
- Data silos and fragmentation occur when information spreads across multiple systems without central visibility.
Solution: Implement data governance programs with centralized discovery tools that map information across the entire technology stack.
- Overly permissive access violates least privilege principles when organizations grant excessive permissions “just in case.”
Solution: Start with zero access and add permissions only when users demonstrate a business need. Review and remove unused privileges quarterly.
- Insider threats and human error cost organizations billions annually through both malicious actions and careless mistakes.
Solution: Combine technical controls like DLP tools with behavioral programs, including security training and anonymous reporting channels.
- Legacy systems often lack modern security features and can’t be easily updated.
Solution: Segment legacy systems on isolated network zones with strict access controls. Prioritize migration to modern platforms while applying compensating controls.
Best Practices for Effective Data Security Management
Organizations that excel at data security follow these proven strategies:
- Apply zero-trust architecture by verifying every access request regardless of network location. Implement micro-segmentation, least privilege access, and assume breach scenarios in your planning.
- Maintain regular patching through automated patch management processes that apply security updates quickly. Test patches in development environments first, but prioritize speed when exploits are actively circulating.
- Conduct audits and penetration tests annually through third-party security assessments. Penetration testers simulate real attacks, exposing vulnerabilities before attackers do. Prioritize remediation based on actual risk.
- Develop and test disaster recovery plans with documented step-by-step procedures for restoring operations. Store recovery plans in multiple accessible locations and test backups regularly through actual restoration exercises.
- Prioritize employee training through ongoing education with monthly tips and simulated exercises. Make training relevant to job roles and celebrate employees who report suspicious activities.
The Future of Data Security Management
Data security continues to adapt to new technologies and emerging threats. Several trends will influence how organizations protect information in 2025 and beyond.
AI and automation: Machine learning algorithms now detect anomalies that would be impossible for humans to spot manually. AI-powered security operations centers analyze millions of events, correlate threats across systems, and trigger automated responses. Predictive analytics help teams stay ahead by identifying attack patterns before they fully form.
Quantum-safe encryption: Quantum computers threaten to break current encryption standards within the next decade. Forward-thinking organizations are implementing quantum-resistant cryptographic algorithms. NIST released its first post-quantum cryptography standards in 2024, and migration planning should start now for systems handling long-lived sensitive data.
Privacy by design: Instead of adding privacy controls after development, teams now build them in from the start. This includes integrating data minimization, consent management, and retention policies into system design.
Securing the Future of Your Data
Data security management is essential for every organization. Strong security practices prevent financial loss, legal penalties, and reputational harm while building lasting trust with customers and partners who expect their information to be protected.
Start with the basics: identify your data, classify it correctly, and apply the right protections. Then strengthen that foundation through continuous monitoring, staff training, and regular updates. Frameworks like NIST and ISO 27001 can guide these improvements as new threats emerge.
At Syracuse University’s iSchool, the Certificate of Advanced Study in Information Security Management and the Information Management and Technology Bachelor’s Degree equip students with the expertise to design, manage, and lead effective data protection strategies. Graduates enter the workforce ready to safeguard organizational assets and drive smarter, safer digital transformation across industries.
Frequently Asked Questions (FAQs)
What is the main goal of data security management?
The main goal is to keep sensitive information safe from unauthorized access, damage, or loss. This means protecting its confidentiality, integrity, and availability while meeting legal requirements and supporting daily operations. Good data security management keeps information secure but still easy for authorized users to access when needed.
How does data security management differ from cybersecurity?
Cybersecurity is the broader practice of protecting all digital assets (networks, systems, devices, and data) from attacks. Data security management is a specialized subset that focuses specifically on protecting the information itself, regardless of where it’s stored or transmitted. While cybersecurity might secure a network perimeter, data security management ensures that even if attackers breach that perimeter, they still can’t access or use the protected data due to encryption and access controls.
Who is responsible for managing data security in an organization?
Data security is a shared responsibility. The CISO or security team leads the strategy and technical setup, but all employees play a part. Executives set budgets and policies, IT staff manage systems, and everyday users handle data safely. Data owners decide who can access information, and IT custodians put those rules in place. Strong security depends on teamwork across the organization.
How can small businesses implement data security management cost-effectively?
Small businesses can start with affordable, high-impact steps like enabling multi-factor authentication, using built-in encryption, setting up automatic backups, and offering basic security training. Focus on protecting key data such as customer info and financial records. Many cloud-based tools provide strong protection at low cost, removing the need for expensive infrastructure.
