Key Takeaways
- Core applications of AI in cybersecurity include threat detection, phishing prevention, behavioral analytics, network security, and identity management.
- The generative AI in the cybersecurity market is expected to grow almost tenfold between 2024 and 2034.
- Future trends in AI for cybersecurity point toward autonomous responses, privacy-preserving AI, and preparing for quantum-resistant security.
Just a few decades ago, the idea of computers writing code or generating images would have sounded like science fiction. However, today, that level of artificial intelligence is something we can easily access every day. We’re surrounded by generative AI, chatbots, as well as various different apps and platforms to the point that AI has become part of everyday life.
Among the many fields transformed by AI is cybersecurity. As digital threats become more complex, organizations are also using different types of AI in cybersecurity to help protect their data.
What Is AI in Cybersecurity?
AI in cybersecurity involves applying artificial intelligence to help protect systems, networks, and data from threats. It’s designed to improve security by analyzing large volumes of information, detecting risks sooner, coordinating faster responses, and supporting more accurate decision-making.
To do this, AI in cybersecurity relies on several advanced technologies. For example, machine learning is a key part of it because it allows systems to learn from past cyberattacks and recognize similar patterns in the future, like spotting unusual login behavior or sudden spikes in traffic. Deep learning builds on this by handling more complex and layered data, helping to identify threats that are harder to detect, such as subtle changes in user activity.
Natural language processing (NLP) also helps AI understand and process written content, such as emails, chat logs, or reports, to find signs of phishing or extract important threat information.
Today, 95% of users agree that AI-powered cybersecurity solutions improve the speed and efficiency of prevention, detection, response, and recovery. That’s why adopting AI is one of the smartest moves for staying ahead of emerging threats and reducing the pressure on human security teams.
Core Applications of AI in Cybersecurity
AI has many uses in cybersecurity. Rather than focusing only on threat response, it strengthens the entire security process—supporting early detection, reducing false alarms, improving access control, and adapting to new risks as they emerge.
Threat detection and intelligence
In the past, threat detection relied on preset rules—if something matched a known pattern, it would be flagged. However, this approach often missed new, unfamiliar threats and generated many false positives.
Now, with AI, systems can recognize unusual activity even if it doesn’t match past attack patterns. For example, if a system suddenly receives large amounts of traffic from a foreign server or a user behaves in a way they never have before, AI can flag it as suspicious.
Over time, machine learning models improve by learning what actual threats look like and adjusting alerts, thus potentially reducing the number of false alarms security teams have to deal with.
Phishing and social engineering prevention
Phishing remains one of the most common ways attackers trick people into giving away personal information or clicking harmful links. Traditional email filters catch many of these, but sophisticated phishing attempts can still slip through.
However, using NLP, AI systems can analyze the tone, content, and structure of emails or messages. So, if something seems off—like the wording is too urgent or the sender’s domain looks suspicious, then AI can detect it and block or flag the message before it reaches the user.
This approach improves the detection of sophisticated attacks and lowers false positives. Rather than blocking safe messages, AI models can learn from user behavior (what they open, ignore, or report) to get better over time.
Behavioral analytics and insider threats
Many cyber threats actually come from inside the organization. It could be intentional, or even someone accidentally misusing their access. Detecting these “insider threats” is tricky because the activity often looks normal on the surface.
AI solves this by using behavioral analytics. It builds a profile of what typical behavior looks like for each user, like what files they access or where they connect from. When someone suddenly does something out of the ordinary, like accessing sensitive files at 3 a.m. or logging in from a different country, AI flags it for review.
This method reduces reliance on static rules and allows for a more personalized, adaptive view of risk.
Endpoint and network security
Endpoints are devices like laptops, phones, and servers, which tend to be common entry points for attacks. If one is compromised, it can affect the broader network. AI helps protect both endpoints and the network.
Where traditional security systems scan for known threats, AI introduces a predictive layer. It can identify new forms of malware, detect odd file behaviors, and monitor unusual communication between devices—even without prior examples.
For example, if an AI-powered system detects ransomware starting to spread from one device, it can isolate that device from the network immediately while notifying the security team. This real-time action helps stop threats before they cause widespread damage.
Identity and access management (IAM)
IAM helps make sure that only authorized users get access to resources. It manages who can log in, what they’re allowed to see, and how those permissions are kept secure over time.
AI strengthens IAM by helping systems decide whether a login or access request is safe in real time. It can analyze risk factors like whether someone is logging in from an unfamiliar device, requesting access to something outside their role, or trying to reach systems they haven’t used before. If the behavior looks risky, the system might block access, require extra verification, or alert an admin.
AI also helps clean up outdated or overly broad permissions, making sure users don’t keep access to things they no longer need. This makes organizations less vulnerable to stolen credentials and accidental exposure.
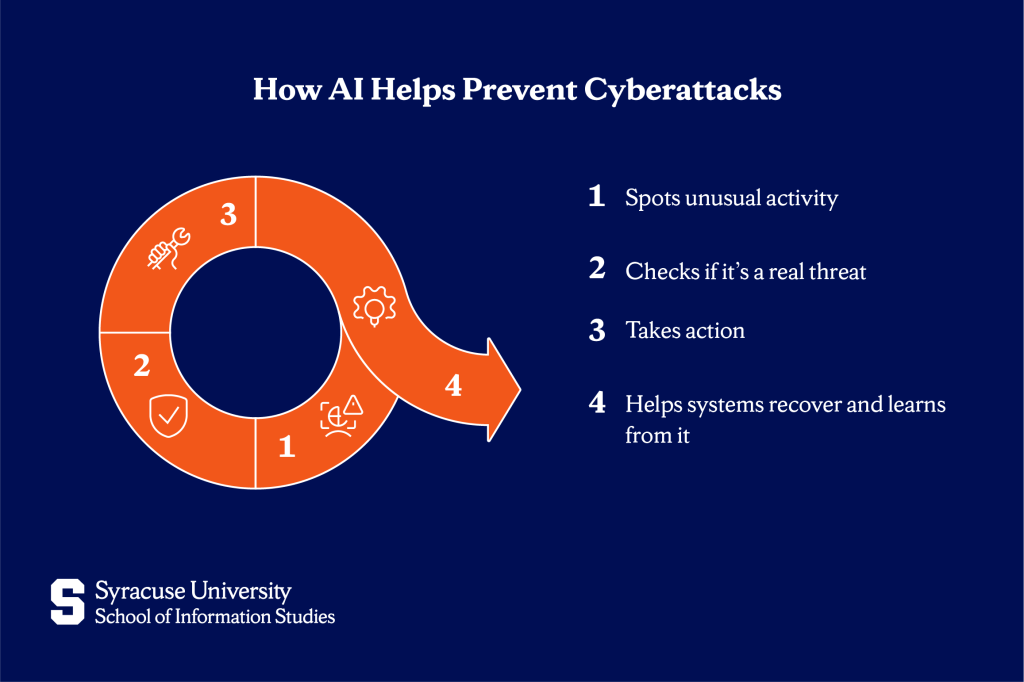
How AI Helps Prevent Cyberattacks
In addition to responding to cyberattacks, AI also plays a key role in stopping them before they cause damage. It does this by powering a complete defense cycle that includes:
- Detection – AI watches for unusual activity, like strange login attempts or unfamiliar network behavior, and quickly spots signs of an attack, even ones it hasn’t seen before.
- Analysis – Once something suspicious is found, AI examines it to figure out what it is, how serious it might be, and what systems could be affected.
- Response – If the threat is real, AI can act fast by blocking access, isolating systems, or sending alerts to stop the attack before it spreads.
- Recovery – After an attack, AI helps systems get back to normal and uses what it learned to spot similar threats more quickly in the future.
Can Cybersecurity Be Safely Automated with AI?
AI has proven to be a powerful tool in cybersecurity, especially when it comes to speed, accuracy, and scalability. In high-risk environments like energy infrastructure, AI-led systems have achieved impressive results—one study found a 98% threat detection rate and a 70% reduction in incident response time. These gains show how AI can help organizations spot and stop attacks far faster than human teams working alone.
That said, full automation comes with trade-offs. While AI can detect patterns and act in real time, it still depends on the quality of the data it’s trained on. If the data changes over time, the system may start to miss threats or produce more false alarms. There’s also the risk of over-automation, where critical decisions are made without enough human oversight, potentially leading to blocked users, disrupted operations, or missed context.
The safest and most effective approach is a balance. AI can handle the heavy lifting: monitoring traffic, spotting anomalies, filtering noise, and reacting quickly to low-risk issues. Meanwhile, human analysts still need to review complex threats, understand context, and make judgment calls that AI can’t.
Generative AI in Cybersecurity
Generative AI has become an integral part of cybersecurity, both as a defense tool and, unfortunately, as a weapon for attackers.
On the offensive side, cybercriminals are using generative AI in order to create more convincing phishing emails, write malware that can better avoid detection, and even generate fake identities or deepfakes and carry out fraud.
Such attacks, which are strengthened through generative AI, tend to be harder to recognize and can be produced at scale, making them more dangerous than traditional methods. Because generative AI can mimic human language and behavior so well, it lowers the effort needed to launch sophisticated, personalized cyberattacks.
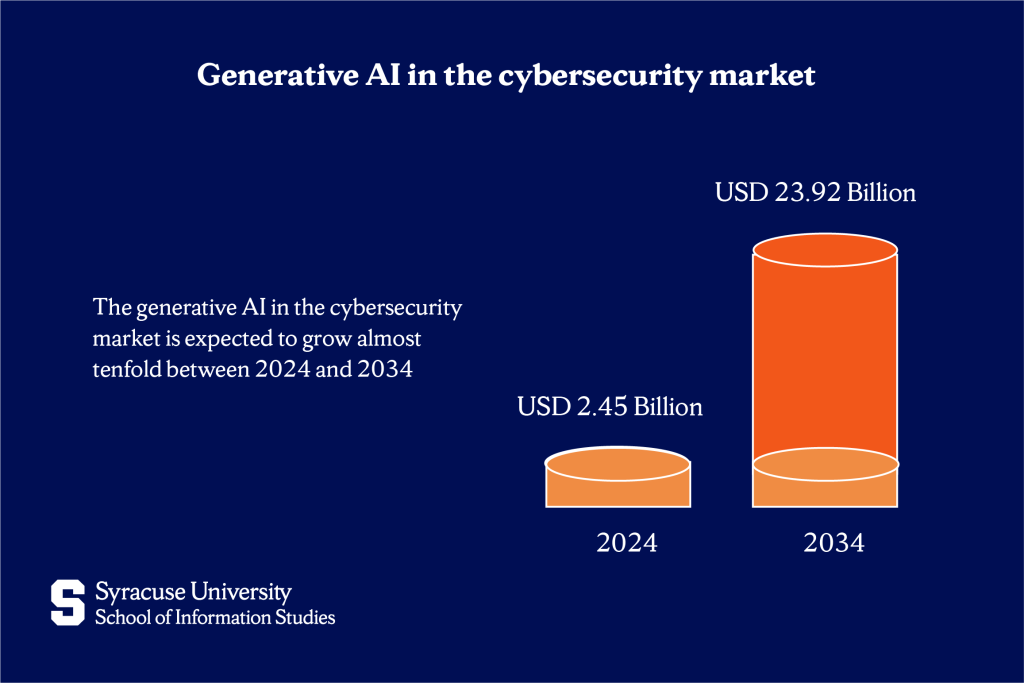
Still, on the defensive side, organizations are also increasingly turning to generative AI to improve their ability to detect and respond to threats. In fact, the generative AI in the cybersecurity market is expected to grow almost tenfold between 2024 and 2034. The growing number of cyberattacks, rising costs of data breaches, and widespread shift to remote work are pushing companies to adopt faster, smarter solutions—and generative AI fits that need.
Sectors like banking, healthcare, and energy are already using generative AI for threat detection, insider risk prevention, and real-time defense, and these areas are projected to grow even faster in the next decade.
Best AI-Powered Cybersecurity Tools
There are many AI-powered tools and platforms that are offered in the market today that center on protecting networks, devices, and data. Some of the most common types of AI-driven cybersecurity tools include:
Endpoint protection platforms
These tools protect individual devices, like laptops and servers, by detecting and stopping malware, ransomware, and other threats using AI-based analysis.
Top choices in the market for these tools include:
- CrowdStrike Falcon
- SentinelOne
- Sophos Intercept X
- Microsoft Defender for Endpoint
AI-powered SIEM & SOAR platforms
These platforms collect and analyze security data from across an organization, helping detect threats faster and automate responses.
Some recognized names in this area are:
- Splunk Enterprise Security
- IBM QRadar
- Palo Alto Cortex XSOAR
- Sumo Logic
Next-gen firewalls (NGFW) with AI
NGFWs use AI to monitor and filter network traffic in real time, blocking advanced attacks and adapting to new threats.
Commonly used platforms for such firewalls include:
- Palo Alto Networks NGFW
- Fortinet FortiGate
- Cisco Firepower
- Check Point Quantum Security Gateway
AI-based NDR (network detection & response)
NDR tools use AI to monitor internal network traffic, detect suspicious behavior, and flag threats that may have bypassed other defenses.
Some popular choices for AI-based NDR include:
- Darktrace
- Vectra AI
- ExtraHop Reveal
- Cisco Secure Network Analytics
Future Trends in AI for Cybersecurity
Although AI has already taken over nearly every aspect of cybersecurity, its role and influence are only expected to grow. The future is focused on responding even faster, protecting privacy even more, and preparing for the new types of risks that will arise.
Three major trends that are guiding the future of AI use in cybersecurity include:
Autonomous response systems
One of the main appeals of certain AI applications is their ability to take action without the need for human intervention. That’s precisely what autonomous response systems are based on.
Powered by AI, these tools can help block suspicious activity or shut down access the moment a threat is identified. This kind of automation helps prevent damage in situations where speed is of the essence, like ransomware attacks.
One of our alumni, Jian Jian, who earned a Master of Science in Applied Data Science from Syracuse University’s iSchool, is now focused on researching and developing AI techniques for cybersecurity products, with a special interest in ransomware detection as a field with growing impact.
Companies that use security AI extensively have saved an average of $1.9 million compared to those that don’t. These systems aren’t designed to replace human teams but to empower them—freeing up time to focus on strategic decisions instead of responding to a constant stream of alerts.
Federated learning for privacy-preserving AI
One challenge with AI is that it often needs lots of data to learn effectively. This is a problem in cybersecurity as, sometimes, the data stored can be highly sensitive. Because of this, federated learning has become a trend.
Federated learning is a way to train AI models across many different devices or locations without ever moving the actual data. For example, a company with offices around the world can let each location’s system train the model using its own data. Instead of sharing the raw information, only the model updates get sent to a central server.
This approach enables the AI to learn and improve while keeping sensitive data where it belongs. It supports compliance with data privacy regulations and helps minimize the risk of exposing confidential information.
AI’s role in quantum-resistant cryptography
Quantum computing is still in early development, but when it becomes more widely used, it could break many of the encryption methods we rely on today. That’s why cybersecurity experts are already working on quantum-resistant cryptography to stand up to quantum-level computing power.
AI is helping in this effort by analyzing how quantum computers might break existing systems and by assisting researchers in designing new, more secure methods.
Final Reflections on AI in Cybersecurity
AI is no longer just a tool added to cybersecurity. It’s become a part of how protection is done, and it’s likely to stay that way. Yet, as its role grows, it can also bring a sense of unease. The idea that AI can take over tasks humans once handled and do them faster and more accurately can feel intimidating.
However, the goal is not to compete with the machines but to learn to work with them and make use of them. That’s precisely what our Applied Human-Centered Artificial Intelligence Master’s Degree at the iSchool is designed for. It’s a program that equips students to build AI systems and to do so with a strong grounding in human values.
AI may be powerful, but with the right training, we can make sure it serves people first. Our program helps you advance technology while staying true to ethical and human-centered principles.
Frequently Asked Questions (FAQs)
What are the ethical considerations of using AI in cybersecurity?
The main concerns about using AI in cybersecurity relate to privacy, bias in AI models, transparency in decision-making, and making sure that automated systems do not violate user rights.
What are the main challenges in implementing AI for cybersecurity?
The main challenges include high implementation costs, data quality issues, lack of skilled professionals, and the risk of over-reliance on automated systems without proper human monitoring.
What kind of skills are required to implement AI in cybersecurity?
To implement AI in cyber security, professionals typically need knowledge of machine learning, data analysis, cybersecurity fundamentals, and programming skills, along with an understanding of ethical and regulatory considerations.
